Cracking passwords from the core Network
Source: DeepNet.Ga
we’ll Intercept passwords is in the core of the network. Now, then sit down more comfortably Freaks, we begin.
Hey freaks ! DeepNet.ga here. lets straight to the point Many users do not even realize that by filling in the login and password when registering or authorizing on a closed Internet resource and pressing ENTER, this data can easily be intercepted. Very often they are transmitted over the network in an unprotected form. Therefore, if the site on which you are trying to log in uses the HTTP protocol, then it is very easy to capture this traffic, analyze it using Wireshark and then use special filters and programs to find and decrypt the password.
DeepNet.ga Official. Author’s content.
Attention! All information is provided for informational and educational purposes only. The author is not responsible for any possible harm caused by the materials of this article.
The best place to intercept passwords is in the core of the network, where traffic of all users goes to closed resources (for example, mail) or in front of the router to access the Internet, when registering with external resources. We set up a mirror and we are ready to feel like a hacker.
Step 1. Install and run Wireshark to capture traffic
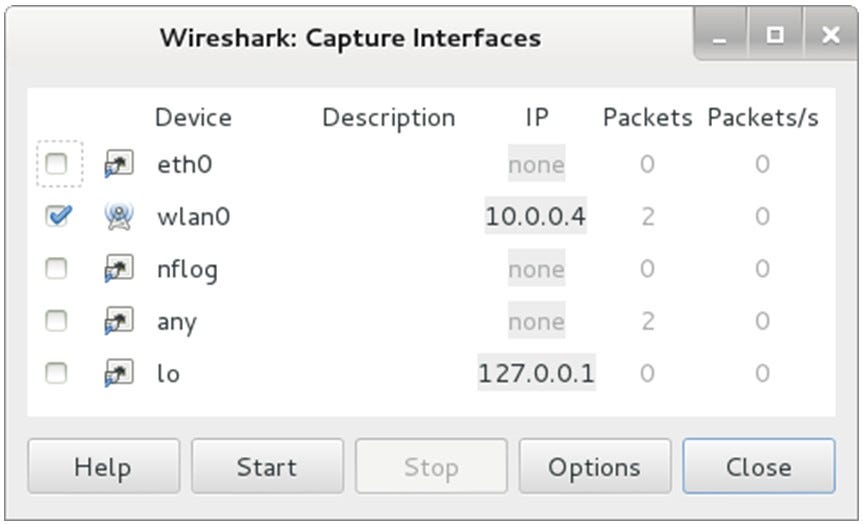
Sometimes it is enough to select only the interface through which we plan to capture traffic and click the Start button. In our case, we capture over the wireless network.
Traffic capture has begun.
Step 2. Filtering captured POST traffic
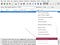
We open a browser and try to log in to any resource using a username and password. Upon completion of the authorization process and opening the site, we stop capturing traffic in Wireshark. Next, open the protocol analyzer and see a large number of packets. It is at this stage that most IT professionals give up because they don’t know what to do next. But we know and we are interested in specific packets that contain POST data that are generated on our local machine when filling out a form on the screen and are sent to a remote server when you click the “Login” or “Authorization” button in the browser.
Introduce a special filter in the window to display captured packets: http.request.method == “POST”
And instead of a thousand packages, we see only one with the data we are looking for.
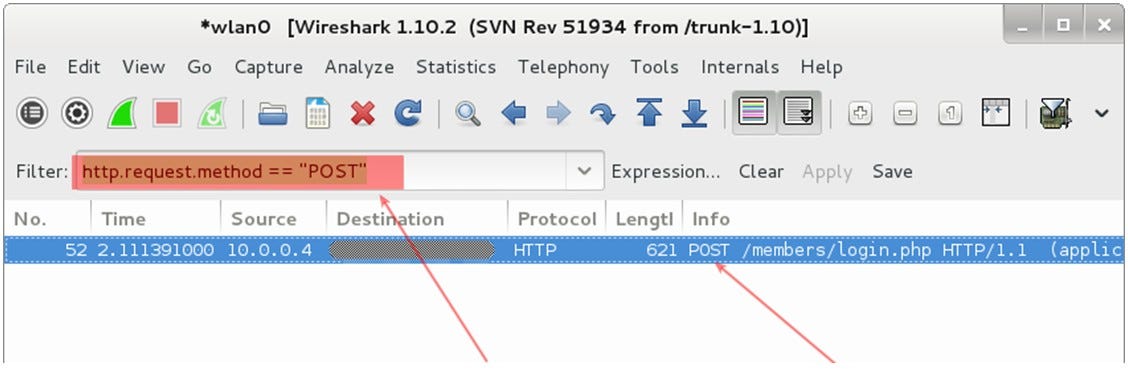
Filtering captured POST traffic — searching for passwords
Step 3. Find the username and password
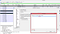
Quick right-click and select Follow TCP Steam from the menu

After that, text will appear in a new window, which in the code restores the content of the page. Let’s find the fields “password” and “user” , which correspond to the password and username. In some cases, both fields will be easily readable and not even encrypted, but if we are trying to capture traffic when accessing very well-known resources such as Mail.ru, Facebook, Vkontakte, etc., then the password will be encoded:
HTTP / 1.1 302 Found
Date: Mon, 10 Nov 2014 23:52:21 GMT
Server: Apache / 2.2.15 (CentOS)
X-Powered-By: PHP / 5.3.3
P3P: CP = “NOI ADM DEV PSAi COM NAV OUR OTRo STP IND DEM”
Set-Cookie: non = non; expires = Thu, 07-Nov-2024 23:52:21 GMT; path = /
Set-Cookie: password = e4b7c855be6e3d4307b8d6ba4cd4ab91; expires = Thu, 07-Nov-2024 23:52:21 GMT; path = /
Set-Cookie: scifuser = networkguru; expires = Thu, 07-Nov-2024 23:52:21 GMT; path = /
Location: loggedin.php
Content-Length: 0
Connection: close
Content-Type: text / html; charset = UTF-8
Thus, in our case:
Username: networkguru
Password: e4b7c855be6e3d4307b8d6ba4cd4ab91
Step 4. Determining the type of encoding to decrypt the password
We go, for example, to the site http://www.onlinehashcrack.com/hash-identification.php#res and enter our password in the identification window. I was given a list of coding protocols in order of priority:
- MD5
- NTLM
- MD4
- LM
Step 5. Decrypting user password
At this stage, we can use the hashcat utility:
~ # hashcat -m 0 -a 0 /root/wireshark-hash.lf /root/rockyou.txt
At the output, we received a decrypted password: simplepassword
Thus, using Wireshark, we can not only solve problems in the operation of applications and services, but also try ourselves as a hacker, intercepting passwords that users enter in web forms. You can also find out passwords to user mailboxes using simple filters to display:
- The POP protocol and filter looks like this: pop.request.command == “USER” || pop.request.command == “PASS”
- IMAP protocol and filter will be: imap.request contains “login”
- SMTP protocol and you will need to enter the following filter: smtp.req.command == “AUTH”
and more serious utilities for decrypting the encoding protocol.
Step 6. What if the traffic is encrypted and using HTTPS?
There are several options to answer this question.
Option 1 . Connect to disconnect the connection between the user and the server and capture the traffic at the moment the connection is established ( SSL Handshake ). At the moment of establishing a connection, you can intercept the session key.
Option 2 . You can decrypt HTTPS traffic using the session key log file recorded by Firefox or Chrome. To do this, the browser must be configured to write these encryption keys to a log file (example based on FireFox) and you should get this log file. Basically, you need to steal the session key file from another user’s hard drive (which is illegal). Well, then grab traffic and use the resulting key to decrypt it.
Clarification. We are talking about the web browser of a person who is trying to steal a password. If we mean decrypting our own HTTPS traffic and want to practice, then this strategy will work. If you’re trying to decrypt other users’ HTTPS traffic without accessing their computers, it won’t work — that’s both encryption and privacy.
After receiving the keys for option 1 or 2, you need to register them in WireShark:
- Go to the Edit — Preferences — Protocols — SSL menu.
- Set the flag “Reassemble SSL records spanning multiple TCP segments” .
- “RSA keys list” and click Edit .
- We enter data in all fields and write the path in the file with the key

WireShark can decrypt packets that are encrypted using the RSA algorithm . If DHE / ECDHE, FS, ECC algorithms are used , the sniffer is not our helper.
Option 3 . Get access to the web server that the user is using and get the key. But this is even more challenging. In corporate networks, for the purpose of debugging applications or content filtering, this option is implemented on a legal basis, but not for the purpose of intercepting user passwords.
Thank you all for your attention!